
A new initiative is helping local organizations respond proactively to the threat of cyber attacks.
Cyber attacks—including data breaches, identity theft, and phishing—are becoming more frequent and more sophisticated every day. For most organizations, the only response is a defensive one: The organization opens an investigation after the attack has occurred. Unfortunately, many organizations do not detect the attacks right away and may not realize their computer systems have been compromised until after much damage has been done.
The Cybercrime Investigation, Research, and Education Initiative (CIRE), developed by Notre Dame’s Center for Research Computing, is partnering with local industries and law enforcement agencies to foster a new approach. It is conducting proactive responses to cyber incidents in an effort to transform cybersecurity in our region.
CIRE’s Proactive Approach
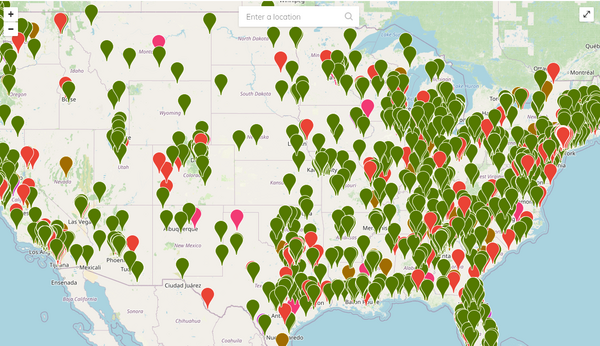
Using a custom web-based interface provided by an industry partner, CIRE detects Indicators of Compromise (IOCs) within computer systems. Examples of IOCs might include IP addresses used by malware, hashes of malicious files, sites used for phishing or malware distribution, and patterns in network traffic that suggest an intrusion has taken place.
The IOCs are then plotted on a map so CIRE can review them in real time.
CIRE uses the map to actively monitor incidents in the region. When it locates one, it initiates an investigation.
The example below shows an IP address that exhibited IOCs in the area of South Bend, IN.
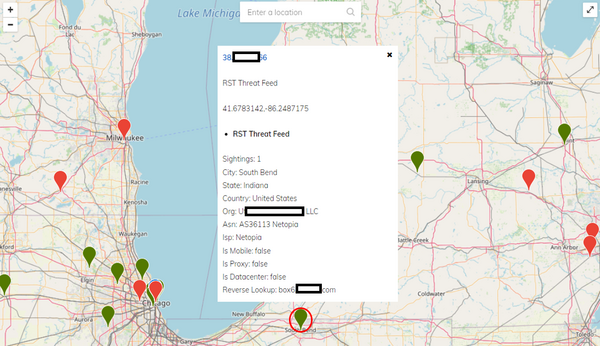
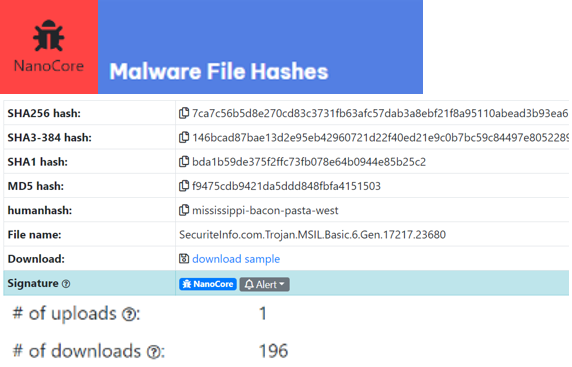
In this example, CIRE used open-source investigative techniques to determine that this IP address was hosting a strain of malware known as NanoCore.
NanoCore is a Remote Access Trojan that enables attackers to remotely execute code on a victim’s system. CIRE determined that the malware was uploaded to the compromised computer once and that it had been distributed 196 times.
Using information of this kind, CIRE can work with local law enforcement partners and obtain a search warrant for the account associated with the IP address. After it identifies the account, CIRE works with law enforcement to obtain a search warrant authorizing the electronic search of the compromised computer.
CIRE uses customized software to forensically extract data from the compromised computer. Then the information can be forensically analyzed in the lab.
Mitch Kajzer, an associate professor of the practice within the Center for Research Computing and managing director of CIRE says, “This project is a novel method to proactively address the growing problem of cyber attacks.” Kajzer, who is executive director of the St. Joseph County Cyber Crimes Unit, added, “The project would not be possible without our partnerships with industry and law enforcement.”
Recently, there have been calls for universities to partner with industry and law enforcement in developing a “digital forensic science strategy.” Kajzer says CIRE’s new project answers that call by taking a “whole-system approach” to addressing the growing problem of cyber crime.
Contact:
Brett Beasley / Writer and Editorial Program Manager
Notre Dame Research / University of Notre Dame
bbeasle1@nd.edu / 574.631.8183
research.nd.edu / @UNDResearch
About The Center for Research Computing:
The Center for Research Computing (CRC) at University of Notre Dame is an innovative and multidisciplinary research environment that supports collaboration to facilitate multidisciplinary discoveries through advanced computation, software engineering, artificial intelligence, and other digital research tools. The Center enhances the University’s innovative applications of cyberinfrastructure, provides support for interdisciplinary research and education, and conducts computational research.
About Notre Dame Research:
The University of Notre Dame is a private research and teaching university inspired by its Catholic mission. Located in South Bend, Indiana, its researchers are advancing human understanding through research, scholarship, education, and creative endeavor in order to be a repository for knowledge and a powerful means for doing good in the world. For more information, please see research.nd.edu or @UNDResearch.